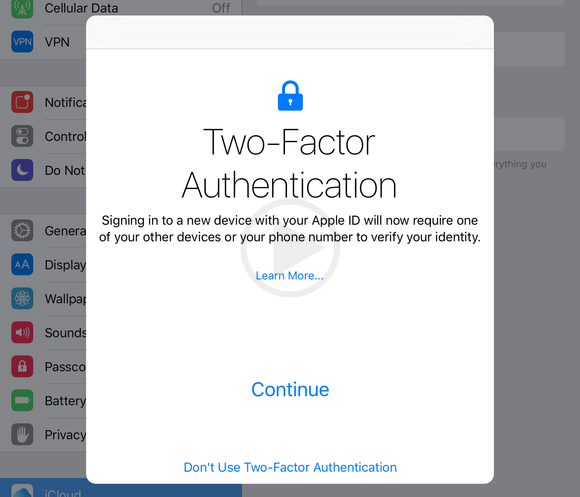
The two factor authentication system of Apple is something that has made us to really sit down and think. This is something which has acted as a replacement for what was there as the verification system earlier. A True 2FA comprises of something you are, something you have and something you knew. This can be typically a password, a token generating or phone device or even a fingerprint.
The factor that comes first is the PIN or password which is not actually a secure thing due to the fact that it can be entered from anywhere. Another factor is the fact that small businesses and consumers have to use a code that is generated as well as sent from another pathway. If you login to Google, Facebook or the Dropbox, you have the choice to use either a onetime password that is generated in the form of an SMS which is sent to your mobile or even though a call. However, if somebody else has access to your phone, then they will get to know what the code may be since they can gain access to by receiving and generating a new code.
The reason why Apple has taken things to another level is so that once the user has set u their devices with the 2FA through their Apple ID, then in order to authenticate that particular device all you need to do is login back again. In order to log into your device, you need to ensure that the device you are attempting from should be trusted and authentic. This may not eliminate the risk involved especially if somebody else has access to your devices physically, however it does help to get rid of most of the potential risks that are present just in case someone is trying to get into your device without your authorization.