This is the second time when another malware has been detected for Macintosh devices. The malwares could easily detect the passwords which has been stored under the macOS Keychain. The security of the Apple that is Apple’s Gatekeeper has succeeded towards blocking the malware and protecting the system effectively. Researchers in the team of the Apple have been detecting the new malware which has stained the OS X.
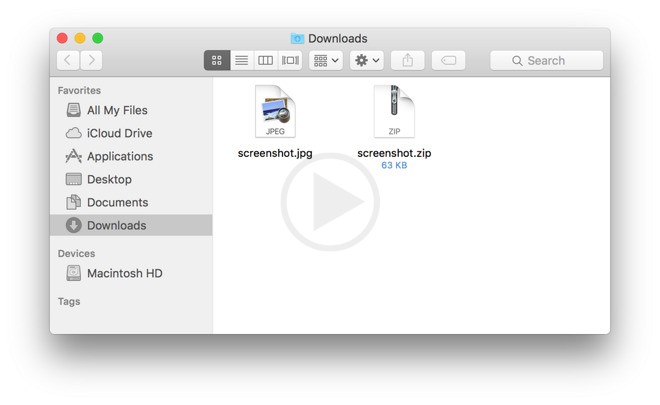
They have been able to get some successful heads up about the malware. They have been able to track that that it is distributed via a compressed .zip file. It contains the text file along with the jpeg file. Once the user clicks on the terminal icon which appears by default in the compressed file, it appears in the dock and closes all the others file. If the user has configured the gatekeeper to execute all the software regardless from which source they appear. IN the backdoor component the malware may get downloaded and run with every reboot done for the system. It may also replace the executable file such as Mach‐O once the user has clicked on the text file in the system.
The malware in the system will automatically start seeking root access into the system. It shall be also waiting for the application to be launched and it will automatically pop up the user dialogues in the system. There are higher chances that the system may be transferred from the owner to the malware by giving it an unwanted access to the system via internal transactions.
The malware may gain access and shall also copy the credentials for Gmail, Facebook and some other login id and passwords such as Amazon and bank details. To fuel Gatekeeper, an internet connection is needed. Apple is trying to find most accurate step to nail down the malware issue.